Performance Tuning Tips for Your Java and .NET Services
A well-oiled application can differentiate between a loyal user base and a graveyard of abandoned carts. This is especially true for Java and .NET services, which power a large chunk of the internet’s functionality.
At MolinaTek, we understand the importance of running your services smoothly. Whether you’re building the next big social media platform or a critical enterprise application, performance tuning holds the key to user satisfaction and scalability.
So, buckle up, developers! Let’s delve into a treasure trove of tips to supercharge your Java and .NET services, transforming them from sluggish snails to supersonic jets.

For the Java Mavericks:
- Embrace the Power of Profiling: Just like a detective wouldn’t jump to conclusions, don’t guess what’s slowing down your Java application. Tools like JProfiler and YourKit provide invaluable insights into your code’s performance bottlenecks. Identify the hot spots – the code sections consuming the most resources – and focus your optimization efforts there.
- Optimize Garbage Collection: Java’s garbage collector (GC) plays a vital role in memory management. However, its default settings might only sometimes be perfect. Analyze your application’s memory usage patterns and adjust GC parameters like heap size and garbage collection algorithms. Tools like VisualVM can help you fine-tune your GC strategy.
- Embrace Immutable Objects: Immutability, the practice of creating objects that cannot be changed after creation, offers a surprising performance advantage. It allows Java to optimize object references and avoid unnecessary memory re-allocation. Consider using immutable classes whenever possible, especially for frequently accessed data.
- Utilize Efficient Data Structures: Choosing the right data structure for the job can significantly impact performance. For instance, a HashMap might outperform an ArrayList for random access, while a StringBuilder is more efficient than string concatenation for creating large strings.
- Cache Wisely: Caching frequently accessed data can drastically improve performance. Consider implementing caching mechanisms at different levels – in-memory caching with libraries like Caffeine or leveraging the built-in caching capabilities of JPA for database queries. However, remember to implement cache invalidation strategies to ensure your data remains fresh.

For the .NET Ninjas:
- Leverage Just-In-Time (JIT) Compilation: The .NET runtime employs JIT compilation, dynamically converting IL code to machine code for improved performance. Ensure your development environment is optimized for JIT compilation by using the latest .NET framework versions and keeping your code well-structured.
- Harness the Power of Asynchronous Programming: Asynchronous programming allows your .NET applications to handle multiple tasks concurrently without blocking the main thread. This is particularly beneficial for I/O-bound operations like network requests and database interactions. Embrace asynchronous libraries like Task Parallel Library (TPL) to create responsive and efficient applications.
- Optimize Code for .NET Framework or Core: When choosing between .NET Framework and .NET Core, consider the specific needs of your application. .NET Core generally offers faster startup times and a smaller footprint, making it ideal for cloud-based deployments or microservices architectures. However, .NET Framework comes with a vast ecosystem of libraries and tools you might leverage.
- Utilize Precompiled Views in ASP.NET: Compiling ASP.NET views beforehand can significantly improve rendering performance. This is because the precompiled views eliminate the need for dynamic compilation at runtime, leading to faster page loads.
Monitor Performance Metrics: Like your car’s dashboard, performance metrics are essential for understanding your .NET application’s health. Tools like Application Insights provide valuable insights into resource utilization, request execution times, and potential errors. Analyze these metrics regularly to identify and address any performance bottlenecks.
Bonus Tip: Embrace a Continuous Improvement Culture:
Performance tuning isn’t a one-time event. It’s an ongoing process that requires continuous monitoring, evaluation, and refinement. Integrate performance testing into your development lifecycle, regularly review your application’s performance metrics, and stay updated with the latest optimization techniques. Remember, small incremental improvements can have a significant impact on the overall performance of your application.
MolinaTek: Your Performance Optimization Partner
At MolinaTek, we empower developers to build high-performing Java and .NET applications. We offer various services, including performance profiling, architecture reviews, and code optimization workshops, to help you achieve the best possible results. Whether you’re just starting or looking to fine-tune existing applications, our team of experienced professionals is here to guide you.
Let’s work together to transform your Java and .NET services into speed demons! Contact us today to discuss your specific needs and learn how MolinaTek can help you achieve optimal performance.
Conquering the .NET Frontier: Your 2024 Guide to Secure Applications

The Wild West of the internet demands a robust security apparatus, and for .NET developers, this translates into a constant quest for the most effective practices. In 2024 the digital landscape will continue evolving, introducing new threats and exciting opportunities.
Here at MolinaTek, we understand the importance of building secure .NET applications. This blog equips you, the intrepid developer, with the latest best practices to fortify your code and safeguard user data.

The Perils of the Frontier: Common Security Threats in 2024
Before venturing into the .NET wilderness, it’s crucial to recognize the lurking dangers. Here are some of the prominent threats developers face:
- Supply Chain Attacks: Malicious actors are increasingly targeting third-party libraries and frameworks. Constantly scrutinize the source and regularly update dependencies.
- API Security Lapses: Insecure APIs can serve as gateways for unauthorized access. Implement robust authentication and authorization mechanisms.
- Server-Side Request Forgery (SSRF): Hackers can exploit SSRF vulnerabilities to execute unauthorized commands on servers. Validate all user inputs and sanitize external requests.
- Open-Source Vulnerabilities: While open-source libraries offer numerous advantages, they can also harbor vulnerabilities. Maintain an updated inventory of your dependencies and patch any known issues promptly.
These are just a few examples, and the threat landscape is constantly shifting. Staying informed and proactive is essential in this dynamic environment.
Arming Yourself for the Journey: Essential Security Practices
Now, let’s equip you with the tools you need to navigate the .NET frontier securely. These best practices are your trusty companions on this quest:
- Embrace Secure Coding Principles:
- Input Validation and Sanitization: Validate all user input to prevent malicious code injection attacks like Cross-Site Scripting (XSS) and SQL Injection. Sanitize user input before storing or processing it.
- Output Encoding: Encode data before displaying it to prevent XSS vulnerabilities. Utilize built-in .NET mechanisms like HtmlEncode or AntiXssEncoder for efficient encoding.
- Implement Strong Authentication and Authorization:
- Multi-Factor Authentication (MFA): Go beyond passwords and utilize MFA to add an extra layer of security. This makes it significantly more difficult for unauthorized users to access accounts.
- Role-Based Access Control (RBAC): Grant users access based on their roles and responsibilities within the application. This minimizes the risk of unauthorized access to sensitive data.
- Harness the Power of Parameterized Queries:
- Prevent SQL Injection: Utilize parameterized queries to prevent attackers from manipulating your database queries. Parameterized queries separate data from the query itself, eliminating injection vulnerabilities.
- Protect Sensitive Data:
- Encryption: Encrypt sensitive data at rest and in transit using industry-standard algorithms. This renders the data unreadable for unauthorized individuals even if they gain access to it.
Hashing: Hash passwords and other sensitive data before storing it in the database. This makes retrieving the original data from the hashed value virtually impossible.

Utilizing the Latest Advancements: Tools and Technologies
The .NET ecosystem offers many tools and technologies to bolster application security. Here are some prominent examples:
- .NET Security Framework: This built-in framework provides authentication, authorization, and cryptography functionalities. Leverage its capabilities to streamline your security implementation.
- Static and Dynamic Application Security Testing (SAST & DAST): These tools identify potential vulnerabilities in your code early in the development lifecycle. Integrate SAST and DAST tools into your development workflow for proactive threat detection.
- Cloud Security Solutions: Many cloud platforms offer built-in security features, such as firewalls and intrusion detection systems. Take advantage of these services when deploying your applications in the cloud.
Security Libraries and Frameworks: The .NET community offers a rich ecosystem of security-focused libraries and frameworks. Explore reputable options like OWASP and AntiXSS to enhance your application’s security posture.
MolinaTek: Your Guide on the .NET Security Frontier
Building secure .NET applications is a continuous journey. At MolinaTek, we guide developers on this path, equipping them with the knowledge and expertise to conquer their security challenges. Our comprehensive training programs and expert mentors empower you to:
- Master secure coding practices
- Implement robust authentication and authorization mechanisms
- Utilize advanced security tools and technologies
Here’s how we can help:
- Security Training and Workshops: Equip your team with the latest security best practices through engaging training sessions and workshops.
- Security Code Reviews: Our security experts can identify and address potential vulnerabilities in your code before they become an issue.
- Security Architecture Consulting: MolinaTech can guide you in designing a secure architecture for your .NET application.
- Stay Ahead of the Curve: We continuously monitor the evolving threat landscape and update our guidance to ensure your applications remain secure.
Conclusion:
By embracing the security best practices outlined above and partnering with MolinaTek, you can build robust and secure .NET applications that inspire trust and confidence in your users. Remember, security is an ongoing journey, not a destination.
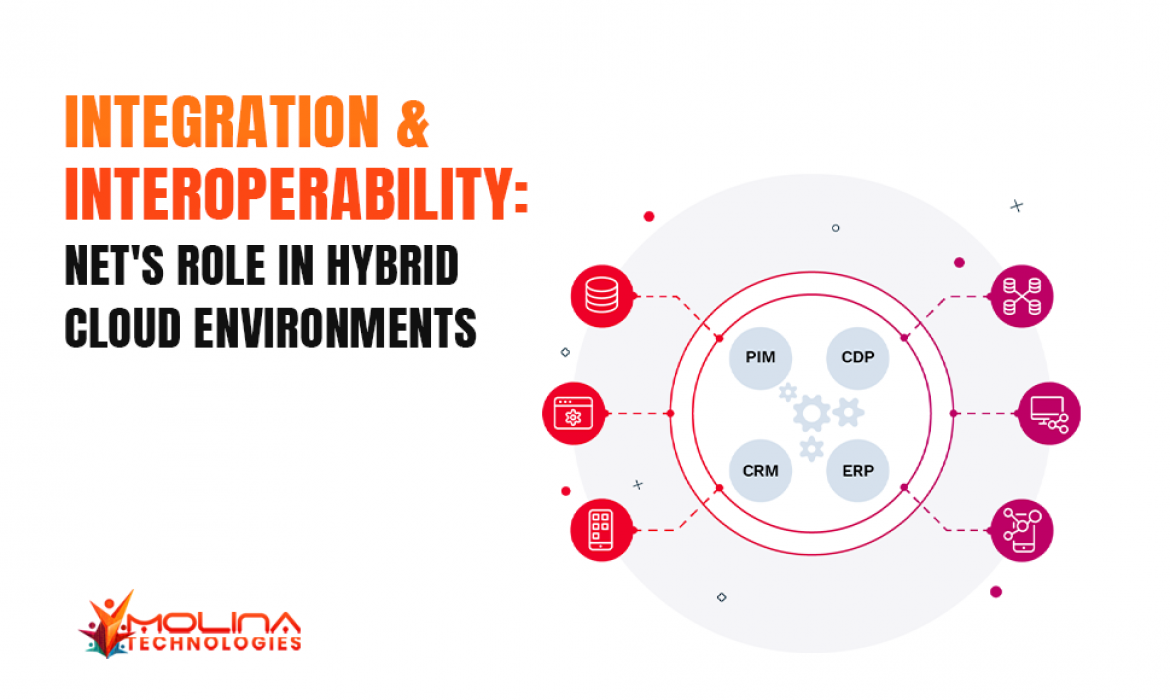
NET’s Role in Integrating Hybrid Cloud Ecosystems
The modern IT landscape is a sprawling sky, dotted with constellations of on-premises data centers, public cloud services, and edge computing nodes. Each offers distinct advantages, but navigating seamless communication between them can feel like scaling. This is where .NET, the versatile developer platform from Microsoft, steps in, offering a lifeline for businesses seeking to integrate and achieve interoperability in their hybrid cloud environments.
A Tale of Two Worlds: The Rise of Hybrid Clouds
Gone are the days of siloed data centers. Businesses today leverage a hybrid approach, strategically distributing their workloads across on-premises infrastructure, public clouds (like Azure, AWS, or GCP), and edge computing solutions. This strategy allows them to reap the benefits of both worlds:
- On-premises data centers offer robust security and control for sensitive data.
- Public clouds deliver unparalleled scalability, pay-as-you-go models, and access to cutting-edge technologies.
- Edge computing brings processing power closer to the data source, minimizing latency and enabling real-time decision-making.
However, this distributed approach wrenches the integration and interoperability equation. Data needs to flow seamlessly between systems, regardless of location or vendor. Here’s where .NET shines.

The .NET Advantage: A Universal Language in a Fragmented Sky
.NET offers a compelling value proposition for building applications in hybrid cloud environments. Let’s delve into its key features that bridge the gap:
- Cross-Platform Compatibility: Developers rejoice! .NET applications can run on a variety of platforms, including Windows, Linux, macOS, and Docker containers. This eliminates the need to rewrite code for different environments, saving time and resources. Imagine building an application that seamlessly connects your on-premises SQL Server database with an Azure-based data analytics service – .NET makes it possible!
- Rich Ecosystem of Libraries and Frameworks: .NET boasts a vast, ever-growing library of pre-built components and frameworks. Developers can leverage these tools to expedite development, ensuring applications adhere to industry standards and best practices. This ecosystem empowers them to focus on core functionalities and innovation rather than reinventing the wheel.
- Language Independence: Don’t get locked into a single programming language. .NET supports various languages, including C#, F#, VB.NET, and even JavaScript (.NET Core). This flexibility allows businesses to leverage developer expertise and preferences, fostering a more productive environment.
- Security at the Forefront: Security is paramount in today’s connected world. .NET prioritizes security throughout the development lifecycle. Features like built-in authentication and authorization tools, coupled with secure coding practices encouraged by the .NET framework, empower developers to build robust and secure applications.
Real-World Applications: How .NET Bridges the Gap
Let’s explore some concrete scenarios where .NET shines in hybrid cloud environments:
- Modernizing Legacy Applications: Many businesses still rely on legacy applications residing in on-premises data centers. .NET can be instrumental in migrating and modernizing these applications for the cloud. Tools like ASP.NET Core allow developers to leverage the power of cloud-native features while maintaining compatibility with existing codebases.
- Building Microservices Architectures: Microservices architectures are a popular choice for building scalable and agile applications. .NET, with its focus on interoperability and containerization, is a perfect fit for developing microservices that can be deployed across different cloud environments. Imagine a hybrid cloud application where the user interface runs on a public cloud for scalability while the backend logic resides securely in an on-premises data center – .NET facilitates this seamlessly.
- Creating Hybrid Data Pipelines: Data is the lifeblood of modern businesses. .NET enables the creation of robust data pipelines that can efficiently collect, transform, and integrate data from various sources, regardless of location. For instance, a . NET-based application can ingest data from an on-premises CRM system, process it in an Azure-based data warehouse, and then visualize the insights back on a web dashboard accessible to employees across the globe.

Beyond Integration: The .NET Symphony’s Encore
.NET’s role in hybrid cloud environments extends beyond just facilitating integration. Its robust features and extensive ecosystem offer additional benefits that contribute to overall success:
- Developer Productivity: With its focus on code clarity and strong tooling support, .NET empowers developers to work efficiently and deliver applications faster. This is particularly beneficial in hybrid cloud environments, where managing distributed codebases can be challenging.
- Security: .NET prioritizes security with built-in authentication, authorization, and encryption features. This is crucial in hybrid cloud deployments, where data security across diverse environments is paramount.
Large Talent Pool: .NET boasts a vast and active developer community. This abundance of skilled professionals allows organizations to tap into a readily available talent pool when building and managing hybrid cloud applications.
.NET: The Indispensable Conductor for Hybrid Cloud Success
In a world of fragmented data and diverse platforms, the ability to integrate seamlessly is no longer a luxury; it’s a necessity. .NET, through its cross-platform capabilities, rich toolset, and commitment to developer productivity, emerges as the ideal conductor for integration within hybrid cloud environments. By bridging the gaps between on-premises and cloud-based resources, .NET allows organizations to leverage the best of both worlds, fostering agility, scalability, and cost-effectiveness. So, as you build your hybrid cloud strategy, consider .NET as the maestro for your integration symphony. With its proven capabilities and ever-evolving suite of tools, .NET ensures your applications sing in unison, delivering a harmonious and successful hybrid cloud journey. MolinaTek gives you that edge in this hay; explore its benefits today by visiting our websites.
The Jigsaw Puzzle of Java: Assembling a Modular Masterpiece with Modules
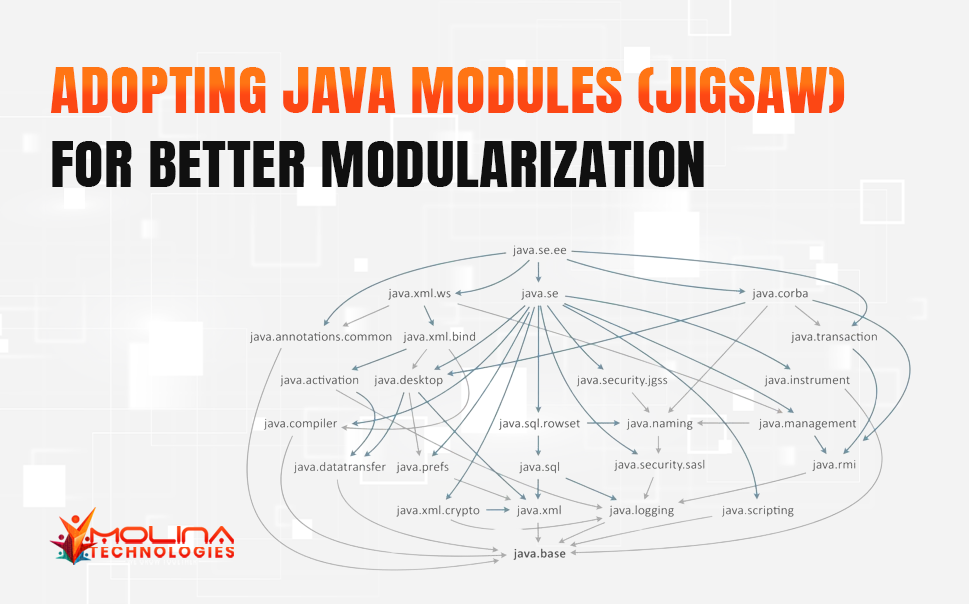
The world of software development thrives on organization. Like a well-oiled machine, each component needs to function seamlessly with others while maintaining its defined role. This principle becomes even more crucial when building large-scale applications, where codebases can sprawl like tangled vines.
For Java developers, the pre-Java 9 era presented a challenge. While packages offered a basic level of organization, they needed to provide the true isolation and encapsulation needed for robust modularity. Enter Project Jigsaw, a revolutionary feature introduced in Java 9 that brought the power of modules (officially known as Java Platform Module System, JPMS) to the table.
Think of JPMS as a jigsaw puzzle for your Java code. Each module represents a piece containing a well-defined set of functionalities and dependencies.

These pieces can then be assembled to create a complete application, but only by interlinking them through explicit declarations. This approach empowers developers with several benefits:
- Enhanced Encapsulation: Modules act like self-contained units, encapsulating their code, data, and resources. This restricts unauthorized access, promoting better code security and maintainability. Imagine a jigsaw puzzle piece with its miniature box – you know exactly what’s inside and how it connects to the bigger picture.
- Improved Dependency Management: With modules, developers explicitly declare the dependencies their module needs to function. This transparency reduces runtime errors caused by missing or conflicting dependencies. It’s like having a clear instruction manual for each puzzle piece, outlining precisely what other pieces it requires to fit in.
- Reduced Classpath Complexity: Prior to JPMS, developers had to wrestle with long and messy classpaths, where every package and library needed to be explicitly referenced. Modules offer a streamlined approach, specifying dependencies directly. Imagine a jigsaw puzzle where each piece has its own connection point, eliminating the need for a sprawling network of puzzle glue.
- Streamlined Development Process: Developers can test and deploy modules independently by isolating modules. This modularity facilitates parallel development, allowing teams to simultaneously work on different application parts. It’s like building a jigsaw puzzle collaboratively; even if teammates work on various sections, they can eventually connect their pieces to create a cohesive whole.
- Stronger Security: Modules grant finer control over access permissions. Developers can define which classes and resources other modules can access, enhancing overall application security. Picture jigsaw puzzle pieces with security locks – only authorized pieces can connect, protecting sensitive information.
Beyond the Basics: A Look at Module Types
JPMS offers a variety of module types to cater to different development scenarios:
- Automatic Modules: These are generated by the Java compiler for existing source code.
- Modular JARs (MJARs): These are JAR files designed explicitly for modules containing the module descriptor and its code.
- Unnamed Modules: These are useful for internal implementation details within an application.
- Open Modules: Designed for sharing public APIs with other modules.
- Modular Services: A specialized type of module offering services to other modules at runtime.

Understanding Potential Challenges
While offering significant advantages, adopting JPMS isn’t without its challenges. Existing legacy codebases might require refactoring to adapt to the modular structure. Additionally, developers need to adjust their workflow and understand the new module declaration syntax.
However, the long-term benefits outweigh the initial learning curve. By embracing the Jigsaw approach, developers can create robust, maintainable, and secure Java applications, paving the way for a more efficient and collaborative development process.
MolinaTek: Your Partner in Building Modular Masterpieces
Are you ready to unlock the power of JPMS in your Java projects? MolinaTech empowers developers with the knowledge and expertise to navigate the modular revolution. We offer comprehensive training programs, workshops, and consulting services to help you leverage the advantages of JPMS effectively.
Challenges and Solutions for Continuous Java & .NET Security
In the ever-evolving landscape of cybersecurity, staying compliant can feel like a never-ending dance. For developers building and deploying Java and .NET services, the challenge is two-fold: ensuring the security of these services and adhering to a growing list of industry regulations. This is where continuous compliance comes into play – a proactive approach to weaving security throughout the development lifecycle.
But before we slip on our dancing shoes, let’s acknowledge the complexities that can trip you up in the compliance tango.

The Challenge: A Symphony of Security Issues
Java and .NET, while robust platforms, are not immune to vulnerabilities. Here are some common culprits that can disrupt your compliance rhythm:
- Open-source dependencies: These invaluable tools often introduce hidden security risks. Outdated libraries or those with known vulnerabilities can become an easy entry point for attackers.
- Misconfigurations: A single typo in a configuration file can expose sensitive data or bypass critical security controls.
- Coding errors: Buffer overflows, SQL injections, and other coding flaws can create exploitable weaknesses in your applications.
- Insider threats: Disgruntled employees or negligent actions can lead to data breaches even with the best security posture.
Compliance Concerns: A Chaotic Chorus
Adding another layer of complexity, businesses must navigate a complex world of industry regulations. These can include:
- General Data Protection Regulation (GDPR): This European Union regulation protects the privacy of EU citizens and imposes strict data handling requirements.
- Payment Card Industry Data Security Standard (PCI DSS): This standard mandates robust security measures for card payment organizations.
Health Insurance Portability and Accountability Act (HIPAA): This US law safeguards sensitive patient medical information.
Navigating the intricate details of these regulations – understanding their specific requirements and ensuring continuous adherence – can feel like an overwhelming chorus.
Solutions that Harmonize Security and Compliance
Fear not, fellow developers! Here are some strategies to transform the compliance tango from a chaotic dance to a smooth, harmonious routine:
- Embrace the Shift-Left Approach: Don’t wait until deployment to address security concerns. Integrate security testing tools throughout the development lifecycle, from code reviews to static analysis. Tools like SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing) can identify potential vulnerabilities early on.
- Automated Security Scanning: Leverage automated vulnerability scanners to continuously monitor your codebases for known security weaknesses. These scans can be integrated into your build pipelines, ensuring prompt detection and remediation.
- Containerization: Containerize your applications to isolate them from the underlying infrastructure. This reduces the attack surface and simplifies security management.
- Secure Coding Practices: Educate your development team on secure coding practices. This includes using strong passwords, validating user input, and properly handling sensitive data. Tools like IDE plugins and code linters can help enforce these best practices.
- Embrace the Power of Open-Source Security Solutions: Many open-source tools and libraries can assist you in your compliance journey. Explore options like security frameworks (e.g., Spring Security), vulnerability scanners (e.g., OpenVAS), and secure coding libraries.
- Continuous Monitoring and Logging: Implement continuous monitoring tools to track suspicious activity and potential breaches in real-time. Robust logging practices are also crucial to effectively identifying and investigating security incidents.
Compliance Management Software: Consider utilizing specialized compliance management software. These platforms can help you streamline your compliance efforts by automating tasks like risk assessments, policy management, and reporting.
MolinaTech: Your Partner in the Compliance Tango
MolinaTech understands the challenges of continuous compliance for Java and .NET services. We offer comprehensive services and resources to help your development team navigate the security landscape and achieve compliance goals.
Here’s how we can support your journey:
- Security Training and Workshops: Equip your team with the knowledge and skills to write secure code and understand compliance requirements.
- Security Assessments and Audits: Gain valuable insights into your security posture through comprehensive security assessments and penetration testing.
- Compliance Consulting: Our expert consultants can guide you through the intricacies of various regulations and help develop a robust compliance strategy.
- Managed Security Services: We offer managed security services, including real-time monitoring, threat detection, and incident response.
Refrain from letting the compliance tango turn into a frustrating fumble. By employing proactive security measures and partnering with a trusted advisor like MolinaTech, you can achieve continuous compliance, build more secure services, and ultimately focus on what matters most – creating innovative and impactful software.
Ready to take the first step? Contact MolinaTek today and let’s harmonize security and compliance in your development journey!
Expert Java and .NET Services | Molinatek Solutions

Containerization has become a potent weapon in the developer’s arsenal. By encapsulating applications within self-contained units, containers offer a plethora of benefits: portability, scalability, and streamlined deployment. However, when containerizing robust services like Java and .NET, navigating the process can feel like scaling a metaphorical Mount Everest. Worry not, intrepid developer, for this blog acts as your trustworthy, guiding you through the best practices for containerizing your Java and .NET services, ensuring a smooth and successful summit.
Base Camp: Choosing the Right Foundation
The journey begins with a crucial decision: selecting the base image. This image forms the bedrock of your container, acting as the operating system and providing the necessary dependencies for your application to run. Here’s where the wisdom of giants like Docker and Microsoft shines through.
The official OpenJDK Docker images offer a reliable and well-maintained foundation for Java applications. These images are available in various flavors, catering to different JDK versions and configurations. Opt for a minimal image, such as openjdk:19-slim, to keep your container footprint lean and secure.
Similar options exist for .NET applications. Microsoft offers a vast collection of official .NET Docker images on the Microsoft Container Registry (MCR). These images come pre-configured with specific .NET SDK versions and frameworks. Select the image that aligns with your application’s requirements. If you’re using ASP.NET Core, consider images like mcr.microsoft.com/dotnet/aspnet:6.0 for a solid base.

Campfire Essentials: Streamlining Your Code
Next, pack your essentials – your application code and dependencies. While throwing everything into the container is tempting, a minimalist approach reigns supreme. Utilize tools like Maven for Java and NuGet for .NET to manage your dependencies efficiently. These tools can create a specific list of necessary libraries, keeping your container image compact and agile.
Ascending the Peak: Multi-Stage Builds for Efficiency
The climb gets steeper, and efficiency becomes paramount. Enter the concept of multi-stage builds. Traditional builds often compile and copy all dependencies into the final image, leading to bulky containers. Multi-stage builds break the process into distinct stages:
- Building Stage: In this stage, utilize a larger image with all the necessary tools for building your application. Compile your code and create your application package.
- Final Stage: Now, switch to a minimal base image. Copy only the essential application package and any runtime dependencies required for execution.
This layered approach drastically reduces the final image size, leading to faster deployments and lower storage requirements.
Overcoming Obstacles: Health Checks and Graceful Terminations
As you traverse the rocky terrain, unexpected challenges arise. To ensure your container’s health, implement health checks. Docker provides a variety of health check mechanisms, allowing you to define checks that ping an endpoint or run custom scripts to verify your application’s functionality. A healthy container ensures a smooth user experience.
But what about graceful termination? Just as you wouldn’t want your server to abruptly shut down, your containerized application deserves the same courtesy. Utilize Docker’s CMD or ENTRYPOINT instructions to specify a startup script that gracefully handles shutdown signals. This allows your application to perform essential tasks like saving data or terminating processes before a complete shutdown.
Reaching the Summit: Security and Secrets Management
Finally, the summit awaits! Security reigns supreme in containerized environments. Never run your container as “root” – instead, choose a non-privileged user with minimal permissions. Docker allows users to be specified during the build process. Furthermore, minimize the number of processes running within your container, lowering the attack surface.
Another crucial aspect is the management of secrets like passwords and API keys. Storing sensitive information directly within your container image is a security nightmare. Instead, leverage Docker secrets or environment variables stored securely in your container orchestration platform like Kubernetes. These variables can then be injected into your container environment at runtime.
Celebrating Success: Tools and Resources for Your Journey
With these best practices, you’ve successfully scaled the containerization peak! A plethora of tools and resources exist to enhance your journey further:
- Docker Hub: A vast repository of pre-built base images for various languages and frameworks.
- MolinaTek Tech Academy: Hone your containerization skills and explore best practices tailored to Java & .NET development.
Kubernetes: Explore container orchestration platforms like Kubernetes to manage complex deployments with multiple containers.
Now, let’s delve into the nitty-gritty of containerizing Java and .NET services. Buckle up, developers, as we explore some key best practices:

Java’s Jitter:
- Embrace Minimal Base Images: The foundation of your containerized Java applications lies in the base image. Resist the urge to use bloated base images. Opt for slim versions like “openjdk:11-jre-slim” for Java or “.NET Core SDK:3.1-slim” for .NET. Remember, smaller images translate to build times and reduce security risks faster.
- Leverage Multi-Stage Builds: A multi-stage build process separates the application build stage from the final image. This allows you to install dependencies during the build stage and copy only the necessary components into the final, slimmer production image. This approach minimizes image size and enhances security.
- Don’t Run as Root: Security is paramount! Avoid running your Java application as the “root” user within the container. Instead, identify the least-privileged user required for the application to function and run it with that identity. This minimizes the potential damage if a vulnerability is exploited.
- Manage Events Gracefully: Don’t just stop your application abruptly! Implement a graceful shutdown mechanism that allows the application to handle pending requests and clean up resources before exiting. This ensures data integrity and a smoother user experience.
- Consider a Docker Registry: As your containerized applications multiply, managing them locally can become a hassle. Explore the use of a Docker registry, like Docker Hub or a private registry, to centralize storage and distribution of your Docker images. This simplifies deployment and streamlines collaboration.
- Embrace Health Checks: Ensure the health of your containerized applications by implementing health checks. These checks can be simple HTTP requests that verify the application’s responsiveness or more complex scripts that dive deeper into application health. Early detection of issues prevents outages and keeps your system stable.

.NET’s Nuances:
- Use Official Base Images: Stick with the official base images provided by Microsoft for your .NET applications. These images are regularly updated and maintained, ensuring compatibility and security.
- Expose Necessary Ports: Identify the ports your .NET application needs to communicate externally, such as the web server port (typically 80 or 443). Don’t expose unnecessary ports, which reduces the attack surface and enhances security.
- Manage ASP.NET Core Configuration: ASP.NET Core applications rely on configuration files. Consider environment variables within the container to manage configuration settings. This promotes flexibility and avoids hardcoding sensitive information like database connection strings within the image.
- Utilize .NET Core Global Tools: .NET Core comes with a handy set of global tools for tasks like publishing applications and managing dependencies. These can be helpful during the build process within your Dockerfile.
- Leverage ASP.NET Core Web Server Options: ASP.NET Core offers various web server options like Kestrel or IIS. Consider using Kestrel within your container for its lightweight nature. However, some scenarios require IIS, which can also be containerized.
- Leverage Dependency Injection: Embrace the power of dependency injection (DI) within your .NET applications. DI allows for loose coupling of dependencies, simplifies unit testing, and facilitates container configuration changes.
This is just the tip of the containerization iceberg, but we hope these best practices provide a solid foundation for your journey.
Remember, the path to containerization mastery is an ongoing adventure. Experiment with the practices outlined above, explore additional resources, and most importantly, enjoy the increased efficiency and agility your containerized services provide!
What Does a Data Engineer Do?
Information is king in today’s data-driven world, but raw data is a chaotic kingdom. Enter the data engineer, the skilled architects who transform this sprawling landscape into usable, organized territories. They are the invisible hands behind the scenes, ensuring the smooth flow of data that fuels insights, innovation, and success.
But what exactly does a data engineer do? Let’s delve into their fascinating domain and unlock the secrets of their craft.
The Data Delvers: Building Pipelines, Not Sandcastles
Imagine a beach with countless grains of sand, each representing a single piece of data. With their analytical prowess, a data scientist are like beachcombers, searching for patterns and hidden treasures within this vast expanse. However, before the scientist can begin their exploration, the data engineer must meticulously construct the tools to access and organize the sand.
This involves building data pipelines, essentially automated pathways that extract data from various sources, clean and transform it into usable formats, and then deliver it to the designated destinations. It’s like building a sophisticated network of waterways, channeling the raw data from its origins (databases, servers, social media platforms) to the processing plants (data warehouses, analytical tools) where it can be refined and analyzed.

Data engineers wear many hats in this process. They are:
- Data Architects: They design the overall infrastructure, laying the groundwork for efficient data flow.
- Data Wranglers: They tame the unruly data sets, cleaning inconsistencies, correcting errors, and ensuring uniformity.
- Coding Conjurors: They wield the power of programming languages like Python and Java to build and automate the data pipelines.
- Technologists: They possess expertise in cloud platforms (AWS, Google Cloud) and big data solutions (Hadoop, Spark) to manage large-scale data processing efficiently.
From Buzzwords to Action: The Daily Grind of a Data Engineer
A data engineer’s typical day is a symphony of tasks, each contributing to the bigger picture of data accessibility and usability. Here’s a glimpse into their workday:
- Morning Meeting Brew: The day often begins with team huddles, where requirements are discussed, new projects are kicked off, and ongoing tasks are assessed.
- Data Source Detectives: They spend time identifying, integrating, and extracting data from diverse sources. This could involve connecting to databases, APIs, or web scraping techniques.
- Data Wrangling Rodeo: Data arrives messy—incomplete entries, inconsistent formats, and duplicates abound. The data engineer wrangles this chaos, meticulously cleaning and standardizing the data to ensure its accuracy and reliability.
- Pipeline Power Plays: Building, testing, and deploying automated data pipelines consumes much of an engineer’s time. These pipelines perform tasks like data transformation, filtering, and validation.
- Monitoring the Machine: Data pipelines are living entities, and keeping them running smoothly requires constant monitoring. Data engineers ensure the pipelines function flawlessly, identifying and troubleshooting any errors or performance issues.
- Innovation Incubator: They constantly explore new technologies and solutions to optimize data pipelines, improve data quality, and enhance overall data management efficiency.

Beyond the Code: The Soft Skills that Make a Data Engineer Stellar
While technical expertise is crucial, a successful data engineer possesses a unique blend of hard and soft skills:
- Problem-Solving Prowess: Data engineers are adept at dissecting complex challenges and designing creative solutions.
- Communication Champions: They bridge the gap between technical jargon and business needs, effectively communicating data-related concepts to technical and non-technical stakeholders.
- Collaboration Connoisseurs: They work seamlessly with data scientists, analysts, and software developers, fostering a collaborative environment that optimizes data utilization.
- Continuous Learning Crusaders: Data technology is rapidly evolving, and data engineers are lifelong learners, constantly upskilling themselves with new technologies and best practices.
Why Data Engineers are the MVPs of the Data Game
Data engineers play a critical role in empowering data-driven decision-making. They are the invisible backbone of many successful data initiatives. Here’s how their expertise contributes to organizational success:
- Unlocking Insights: By providing clean, accessible data, data engineers empower data scientists and analysts to unearth valuable insights and trends, leading to informed business decisions.
- Streamlining Operations: Data pipelines automate data movement, freeing up valuable time and resources for other critical tasks.
- Improving Decision Making: By providing reliable and consistent data, data engineers ensure that decisions are based on facts, not hunches.
- Enhancing Efficiency: Optimized data pipelines improve data processing speed and facilitate faster response times to changing market conditions.
The Future of Data Engineering: A Bright Horizon
The data landscape is constantly evolving, and the role of data engineers is poised for even greater significance. Emerging technologies like big data, machine learning, and real-time analytics will demand even more sophisticated data pipelines. Data engineers who can adapt and embrace these new technologies will be highly sought after in the coming years.
The data engineers are the silent heroes in the data revolution. They are the builders and architects behind the scenes, ensuring the smooth flow of information that fuels the insights driving businesses forward.
Are you intrigued by the world of data engineering? Do you possess the skills and the passion to navigate the data jungle? MolinaTech can help you unlock your potential and embark on a rewarding career as a data engineer.
Decoding the Data Deluge: 5 Steps to Becoming a Data Engineer in 2024
The digital age has ushered in a tidal wave of data. Every click and action, from social media interactions to financial transactions, leaves a digital footprint. This immense volume of data, often referred to as “Big Data,” has become a game-changer across industries. Businesses increasingly rely on skilled data engineers, the architects who build the pipelines to collect, store, and analyze this valuable resource.
If you’re intrigued by the prospect of building the infrastructure for a data-driven future, carving a path as a data engineer might be your ideal career move. But with the ever-evolving landscape of technology, navigating the journey can seem daunting. Here’s a roadmap to guide your steps and equip you for success in the thrilling world of data engineering in 2024:

Step 1: Solidify Your Foundational Knowledge:
Building a sturdy house requires a strong foundation. Likewise, becoming a data engineer necessitates a solid grasp of core concepts. This includes a strong understanding of:
- Programming Languages: Python remains the undisputed champion in the data engineering realm. Its versatility and extensive libraries like Pandas and NumPy make it perfect for data manipulation and analysis. However, familiarity with SQL, the language for interacting with relational databases, is equally crucial. Additionally, consider acquiring skills in languages like Java or Scala, depending on the specific needs of your chosen domain.
- Mathematics: Data engineering isn’t just about coding; it’s about understanding the math behind the data. Brush up on your linear algebra, probability, and statistics. Familiarity with calculus and discrete mathematics will also prove advantageous.
- Databases: Data is the lifeblood of a data engineer. Understanding different database paradigms – relational (e.g., MySQL) and NoSQL (e.g., MongoDB) – is key to effectively storing and retrieving data relevant to your projects.
Step 2: Master the Art of Data Wrangling:
Data, in its raw form, could be more organized and structured. Data wrangling refers to cleaning, manipulating, and transforming this raw data into a usable format for analysis. Tools like Apache Spark, a distributed computing framework, prove invaluable in handling massive datasets. Consider mastering its functionalities like data partitioning, transformations, and aggregations.
Step 3: Embrace the Cloud:
Cloud computing has revolutionized data storage and processing. Platforms like Google Cloud Platform (GCP), Amazon Web Services (AWS), and Microsoft Azure offer scalable and cost-effective solutions for managing data infrastructure. Familiarize yourself with cloud storage solutions like S3 on AWS or Google Cloud Storage, and delve into cloud-based data processing services like AWS EMR or Google Cloud Dataproc.
Step 4: Sharpen Your Problem-Solving Skills:
Being a data engineer is akin to being a detective. You’ll encounter complex challenges that demand creative solutions. Hone your problem-solving skills by actively participating in online coding challenges on platforms like HackerRank or LeetCode. These platforms offer a plethora of data-focused problems that will test your ability to think critically and find efficient solutions.
Step 5: Build Your Portfolio and Network:
Building a portfolio showcasing your data engineering prowess is crucial to grab the attention of potential employers. Consider participating in open-source projects on platforms like GitHub. This allows you to demonstrate your skills collaboratively while contributing to real-world projects. Additionally, you can actively network with data professionals on platforms like LinkedIn. Attend industry conferences and engage in online forums to connect with peers and expand your knowledge base.

Bonus Tip: Stay Curious and Continuously Learn:
The world of data engineering is constantly evolving. New technologies and frameworks emerge at a rapid pace. Cultivate a spirit of lifelong learning. Stay updated on the latest trends by following industry blogs and attending webinars. Consider pursuing relevant certifications offered by platforms like Coursera or Udacity to validate your skills and enhance your professional credibility.
Becoming a data engineer in 2024 presents a compelling opportunity to be at the forefront of a data-driven world. By following these steps, building your skillset, and fostering a passion for data exploration, you’ll be well-equipped to navigate the exciting journey toward a fulfilling career in data engineering. Remember, the road to success requires dedication and continuous learning. But with the proper guidance and unwavering motivation, you can decode the data deluge and unlock your full potential as a data engineer in a dynamic, data-centric era.
MolinaTek Empowers Your Data Engineering Journey:
At MolinaTech, we understand the challenges and aspirations of aspiring data engineers. We offer comprehensive training programs, mentorship from industry veterans, and career guidance to equip you with the skills and knowledge to thrive in the data engineering domain.
Cloud Data Engineering Certification course with Placement in USA
The American tech dream beckons – a land brimming with innovation, opportunity, and the potential to shape the future. But for aspiring Indian IT professionals, the path can often feel shrouded in mystery. Fear not, for this blog is your decoder ring, unlocking the secrets to propelling yourself into the coveted realm of US Cloud Data Engineering!
The Cloud Craze: Why It’s Raining Jobs
Cloud computing has become the undisputed king of the tech world. Businesses of all sizes are migrating to the cloud, seeking agility, scalability, and cost-effectiveness. This burgeoning landscape is a gold rush for skilled Cloud Data Engineers – the architects and engineers who build, manage, and maintain the intricate data pipelines that power cloud-based applications.

The American Advantage: A Land of Opportunity
The US tech market, a global leader, offers unparalleled opportunities for Cloud Data Engineers. Here’s why:
- Plentiful Jobs: The demand for Cloud Data Engineers in the US far outstrips the available talent pool. This means a competitive salary and a secure career path.
- Cutting-Edge Tech: US tech companies are at the forefront of innovation, offering the chance to work with the latest cloud technologies and projects.
- Thriving Ecosystem: The US boasts a vibrant tech ecosystem with ample networking opportunities and a culture of continuous learning.
Bridging the Gap: The Challenges (and Solutions!)
The American dream may be alluring, but navigating the path can be tricky. Here are some potential hurdles and how MolinaTech’s Cloud Data Engineering Certification Course with Placement assuages them:
- Knowledge Gap: The US tech market seeks professionals with specific Cloud Data Engineering skills and certifications. MolinaTech’s course equips you with the necessary knowledge and hands-on experience through industry-recognized certifications like AWS Certified Solutions Architect – Associate or Microsoft Azure Data Engineer Associate.
- Cultural Differences: Adjusting to a new culture can be daunting. MolinaTech’s course includes cultural sensitivity training and interview preparation techniques tailored to the US job market.
- Visa Labyrinth: The US visa process can be complex. MolinaTech offers personalized guidance on navigating the visa application process and securing work authorization.

MolinaTech: Your Personalized Pathway to US Cloud Data Engineering Success
MolinaTech isn’t just another training provider. We’re your trusted partner in achieving your American tech dream. Here’s what sets our Cloud Data Engineering Certification Course with Placement apart:
- Expert-Led Instruction: Our instructors are seasoned Cloud Data Engineers with extensive industry experience. They don’t just teach; they share real-world insights and best practices.
- Comprehensive Curriculum: Our curriculum is meticulously crafted to cover all the essential Cloud Data Engineering concepts, tools, and technologies. Get ready to delve into data warehousing, data pipelines, big data processing, and cloud security.
- Hands-on Learning: Forget rote memorization. Our course emphasizes hands-on learning through real-world case studies and projects that simulate real-world Cloud Data Engineering challenges.
- Personalized Career Coaching: We understand your unique journey. Our dedicated career coaching team will help you craft a compelling resume, refine your interview skills, and connect you with top US tech companies through our extensive network.
- Mock Interviews: Our fake interview sessions replicate real-world hiring scenarios, equipping you with the confidence and composure to ace your US job interviews.
- Visa Assistance: Let us take the stress out of the visa application process. Our team will guide you through the paperwork and advise you on securing your work authorization.
Beyond the Course: A Lifelong Support System
Your success is our mission. MolinaTech’s support extends beyond the completion of your course. We offer:
- Job Placement Assistance: We leverage our vast network of US tech companies to connect you with potential employers.
- Networking Opportunities: Access exclusive networking events and connect with industry professionals to jumpstart your career.
- Alumni Network: Become part of our vibrant alum network and connect with fellow Cloud Data Engineers who can offer mentorship and support.
The Investment in Your Future
MolinaTech’s Cloud Data Engineering Certification Course with Placement is an investment in your future. The return on investment? A lucrative career in the heart of the US tech scene, working on cutting-edge projects and living the American dream.
What You’ll Learn
Our comprehensive Cloud Data Engineering Certification Course covers a wide range of topics, equipping you with the skills to excel in the US tech industry. Here’s a sneak peek:
- Cloud Fundamentals: Gain a solid understanding of the core concepts of cloud computing, including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS).
- Big Data Technologies: Learn to work with big data tools like Hadoop, Spark, and Kafka, essential for managing and analyzing massive datasets.
- Data Warehousing and Data Lakes: Understand the difference between data warehouses and data lakes, and how to design and implement them for efficient data storage and retrieval.
- Cloud Data Platforms: Master popular cloud data platforms like AWS, Azure, and GCP, gaining expertise in their specific tools and services.
- Data Pipelines and Automation: Learn to build efficient data pipelines that automate data movement and processing within the cloud environment.
- Data Security and Governance: Understand critical data security principles and compliance regulations for handling sensitive data in the cloud.
Ready to Take Flight?
The cloud beckons and MolinaTech is here to equip you with the wings to conquer it. If you’re an Indian IT professional with a thirst for knowledge and a yearning for a successful career in the US tech sector, our cloud data engineering certification course with placement assistance could be the perfect springboard.
Charting Your Course: How IT Training and Placement Services Can Guide Your Career Potential

The tech industry is dynamic, with potential for those seeking fulfilling and lucrative careers. But navigating this ever-evolving field can feel like deciphering a complex code – especially if you’re new to the scene. That’s where IT training and placement services come in, serving as your compass and guide on the path to a rewarding career in technology.
Demystifying the Tech Jungle: The Power of IT Training
Imagine a world where you can transform your passion for technology into a thriving career. IT training empowers you to do just that. Whether you’re a recent graduate, a career switcher, or someone seeking to upskill, these programs equip you with the essential knowledge and practical skills employers seek in the tech sector.
Gone are the days of rote memorization and dry lectures. Modern IT training programs adopt a hands-on approach, allowing you to:
- Master the fundamentals: Gain a solid understanding of core IT concepts, programming languages, operating systems, and networking principles.
- Develop in-demand skills: Learn industry-standard tools and technologies, from cloud computing and cybersecurity to data analysis and software development.
Sharpen your soft skills: Hone your communication, teamwork, and problem-solving abilities – crucial assets in any tech environment.

Beyond the Classroom: Placement Services Pave the Path to Success
The journey doesn’t end with acquiring technical expertise. IT training and placement services go the extra mile to ensure your smooth transition into the workforce. Here’s how:
- Career guidance: Benefit from personalized career counseling, helping you identify your strengths, interests, and career goals within the vast IT landscape.
- Resume and portfolio building: Craft a compelling resume showcasing your newly acquired skills and experience, along with a portfolio demonstrating your practical abilities to potential employers.
- Mock interviews and interview preparation: Gain valuable practice through mock interviews, allowing you to refine your communication skills and build confidence before the real deal.
- Industry connections: Leverage the program’s network of employers to gain access to exclusive job opportunities and connect with hiring managers from leading tech companies.
Job Search Assistance: Benefit from guidance on navigating online job boards, networking strategies, and crafting targeted cover letters that resonate with potential employers.
Unlocking a World of Possibilities: Career Opportunities in IT
The beauty of the tech industry lies in its diverse range of career paths. With the proper training and guidance, you can explore a multitude of opportunities, such as:
Software Development: The Architects of the Digital Age
Imagine weaving intricate tapestries of code and crafting applications that power our daily lives. Software developers are the masterminds behind the scenes, conceptualizing, designing, developing, and testing software solutions that cater to many needs. From user-friendly mobile apps to complex enterprise systems, their expertise drives our world’s technological advancements.
Cybersecurity: Guardians of the Digital Frontier
In a world increasingly reliant on interconnected systems, the need for vigilant protectors is paramount. Cybersecurity professionals are the brave defenders of the digital realm, safeguarding sensitive information and critical infrastructure from cyber threats. They possess a comprehensive understanding of security protocols, intrusion detection techniques, and incident response strategies, constantly innovating to stay ahead of evolving cyber threats.
Network Administration: The Masters of Connectivity
The intricate web of networks that connect people and devices across the globe forms the backbone of our digital communication. Network administrators are the silent heroes behind the scenes, ensuring these complex systems’ smooth operation and maintenance. They possess the expertise to configure, manage, and troubleshoot network issues, providing seamless data flow and uninterrupted connectivity.
Data Analysis: Unveiling the Hidden Gems of Information
In today’s data-driven world, the ability to extract meaningful insights from vast datasets is a crucial skill. Data analysts are the alchemists of information, transforming raw data into actionable insights that empower businesses to make informed decisions. They leverage their expertise in statistical analysis, data mining techniques, and data visualization tools to uncover hidden patterns and trends, guiding strategic decision-making across various industries.
Cloud Computing: Embracing Scalability and Flexibility
The cloud computing revolution has transformed the way businesses store and manage data. Cloud computing professionals are the architects and engineers of this paradigm shift, designing, implementing, and managing cloud-based solutions that offer businesses unmatched scalability and flexibility. They possess the technical know-how to navigate the intricacies of cloud platforms, ensuring efficient resource allocation and optimal performance for businesses of all sizes.

Beyond the Core: Expanding Your IT Horizons
While these five domains represent the foundational pillars of the IT landscape, the world of technology extends far beyond them. Here’s a glimpse into some additional specializations that broaden your career prospects:
- Data Engineering: Architects of data pipelines, ensuring the seamless flow and transformation of data across various systems.
- QA Testing: The quality assurance sentinels meticulously test software applications to identify and rectify any glitches or errors before they reach users.
- BMC Remedy: Specialists adept at managing and troubleshooting IT service desk solutions, ensuring efficient resolution of user issues.
- Java and .Net: Programming languages that empower developers to create robust and versatile software applications for diverse platforms.
- The Investment in Your Future: Choosing the Right Training and Placement Partner
- With so many options available, choosing the right IT training and placement program is crucial. Look for a reputable provider with a proven track record of success. Here are some key factors to consider:
- Curriculum: Ensure the program aligns with your career goals and offers comprehensive training in relevant IT skills.
- Industry partnerships: Seek a program with established connections to leading tech companies, increasing your chances of placement.
- Career support services: Look for programs that offer personalized career guidance, resume-building assistance, and interview preparation.
- Cost and financing options: Choose a program that fits your budget and explore financing options if available.
Investing in Yourself: The Return on Your IT Training Journey
The decision to embark on an IT training and placement program is an investment in your future. By equipping yourself with the necessary skills and knowledge, gaining valuable industry insights, and leveraging the support of placement services, you significantly increase your chances of landing your dream job in the ever-evolving tech landscape.
Consider this: the U.S. Bureau of Labor Statistics projects a 13% growth in computer and information technology occupations between 2020 and 2030, much faster than the average for all occupations. This translates to a projected creation of 531,800 new jobs in the field during that decade. By proactively equipping yourself with the necessary skills and qualifications, you position yourself as part of this exciting growth trajectory.
Embrace the Future with Confidence: Take the First Step Today
The tech industry beckons, offering a world of possibilities and growth. By investing in yourself through IT training and placement services, you equip yourself with the skills, knowledge, and confidence needed to unlock a rewarding career in technology. Take the first step towards your brighter future – explore your options today!
Remember, MolinaTech is here to guide you on your journey. We offer comprehensive IT training programs and dedicated placement services to help you achieve your career aspirations in the ever-evolving world of technology.